Utimaco Enterprise Key Management (ESKM)
The most interoperable and integrated Key Manager – Secure Keys for Data at Rest, in Use, and in Motion
Every organization has customer and employee data that must be protected. ESKM guards against organized attacks, misuse, and data breach exposure which can result in the loss of sensitive data, as well as harm a company’s reputation and brand.
Encryption is easy, and although key management may be difficult, it’s certainly not impossible. ESKM secures keys and provides centralized key management, saving time and money.
ESKM is the first industry-certified Key Management Interoperability Protocol (KMIP) v2.1 offering with market leading support for partner applications and pre-qualified solutions, integrating out-of-the-box with varied deployments, as well as custom integrations.
Key Control and Management through a single pane of glass
- Controls and manages all keys for auditing controls with digitally signed logs and key lifecycle activities
- Reduces audit costs and accelerates visibility
Streamlining Data and Processes
- Unified enterprise key management
- Reliable policy controls
- Centralized administration and audit trails to assist in control attestation
Easy Deployment and Simple Licensing
- Install, configure and simply drop in ESKM as hardware or as a virtual application.
- Access transparent client licensing, without hidden costs attached to volume of keys or scalability
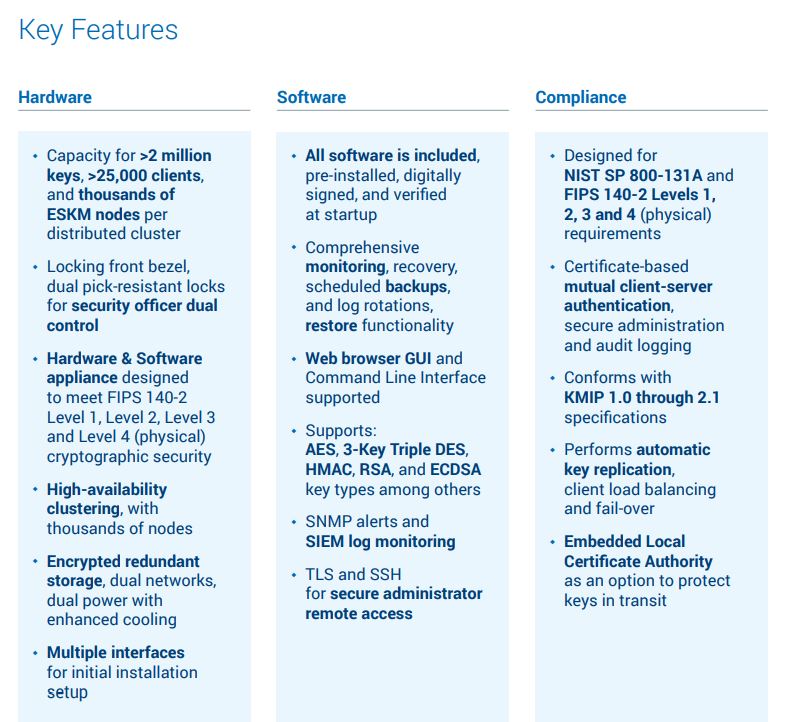
Hardware-based Security on highest level
- Locking front bezel and dual pick-resistant locks provides security officers with dual control
- Security hardened Linux-based server appliance; designed as cryptographic module for FIPS 140-2 Levels 1, Level 2, Level 3 and Level 4 use cases
- Supports mirrored internal storage, dual networks, dual power, and redundant cooling
- Provides a terminal interface (serial RS-232C) and VGA for initial installation setup
Included Software for easy use
- Allows comprehensive monitoring, recovery, scheduled backups, and log rotations, restore functionality
- Web browser GUI and Command Line Interface supported
- Supports (among others): AES, 3-Key Triple DES, HMAC, RSA, and ECDSA key types
- Provides SNMP alerts and SIEM log monitoring
- Provides TLS and SSH for secure administrator remote access
Fulfills various compliance requirements
- Designed for NIST SP 800-131A and FIPS 140-2 Levels 1, Level 2, Level 3 and Level 4 requirements
- Certificate-based mutual client-server authentication, secure administration, and audit logging
- Common Criteria Evaluation Assurance Level (EAL 2+) certified
- Conforms with KMIP 1.0 through 2.1 specifications
- Performs automatic key replication, client load balancing, and fail-over
- Embedded Local Certificate Authority as an option to protect keys in transit
Single and centralized root of trust
- Stores the keys used for cryptographic functions by using the foundation on which all secure operations (including key retrieval of vESKM) depend upon
- Enables an inherently trusted ecosystem
Portfolio Support
- Further protection of keys at rest by integration of the Utimaco CryptoServer LAN HSM
- Full integration of vESKM (virtual appliance for FIPS 140-2 Level 1 use cases) with the UTIMACO GP Hardware Security Module: CryptoServer LAN V5
- Integration of ESKM L3 and L4 (physical) with embedded CryptoServer PCIe card
Robust Scalability and High Availability
- Geographically separates clusters across datacenters
- Thousands of clients, thousands of virtual or hardware appliances and millions of keys are supported
- Highly redundant hardware and failover
Convenient Administration
- Configuration and automated keys replication through active-active cluster
- Allows for hands-off administration
- Performs automated backups and audit logging
Most Interoperable
- Support for partner applications and pre-qualified solutions through the first industry-certified Key Management Interoperability Protocol (KMIP)
- OASIS KMIP allows communication with clients for key management operations on cryptographic material, including symmetric and asymmetric keys, certificates and templates
- Streamlines security policies with a single approach for consistent controls and compliance audits through moving to KMIP
- Both time and cost effective – a single system to learn, control, maintain and audit, as well the ability to integrate new applications without having to reinvest in management
- Avoid vendor lock-in and outdated technology
- Enforces best practices with universal, automated key lifecycle controls
Custom Integrations and Scaled Deployments
- Simplified RESTful API interface for key CRUD (Create, Read, Update, Delete) operations and crypto
- Supports open client libraries such as KMIP, OpenKMIP and PyKMIP
- Implements auto-registration with its native XML-based KMS protocol
- Supports the widest client integrations in the industry
Integrates with largest HPE ecosystem and third-party applications
- ESKM KMIP Integrations (BDT, Bloombase, Brocade, Cryptosoft, ETI-Net, Fornetix, Hitachi Vantara, IBM DB2, MongoDB, NetApp, OpenStack community, Project 6 Research, Quantum, Spectra Logic, Suse, Vmware, ZettaSet)
- HPE Security and Storage Solutions (Helion (OpenStack Barbican + HPSE), MF Autonomy (Connected MX Backup/Recovery), Nimble, NonStop, Secure Encryption (Proliant/smart array controller), SimplyVity/Hyper Converged, StoreEver, StoreEver Tape Library, StoreOnce, StoreServe 3PAR, XP, XP Storage)
Lower your costs and scale key management with Virtual Enterprise Secure Key Manager (vESKM)
- A virtual appliance is easily deployed
- For high availability
- Easy expansion within an existing environment
- Centralizes cryptographic processing, security policies and key management in a FIPS 140-2 Level 1 compliant platform
- Easily implement a virtual key management strategy